Technology
Unlike business applications, Cybersecurity intelligence solutions must essentially follow cyber criminals using the very tools and technologies they rely on.
Essentially, most tools are, or are based on, open source technologies – and range from dedicated Linux distributions, Python scripts, Tor browsers, Java utilities and many more – all loosely clubbed under OSINT tools (Open Source Intelligence).
There is a complete community of tool developers, white hat hackers, market places and thousands of experienced cybersecurity experts that are all baked into the technology platform that powers watchOUT.
As you will see from the Architecture notes the technology must essentially be extremely flexible to accommodate additions and changes on-the-fly. As the technology itself learns from the massive amount of data it ingests, and as the cybersecurity analysts keep nudging and tweaking the tool sets, we must use technology that supports this fluid nature.
Persistence
MySql, ElasticSearch, MongoDB
Languages
Python, Java
Cloud
AWS, on-premise, co-located servers

User Interface
Django
Operating System
Kali Linux

Browser
Tor
Resources
Qualified and experienced Cybersecurity experts
Toolset
OSINT and proprietary code
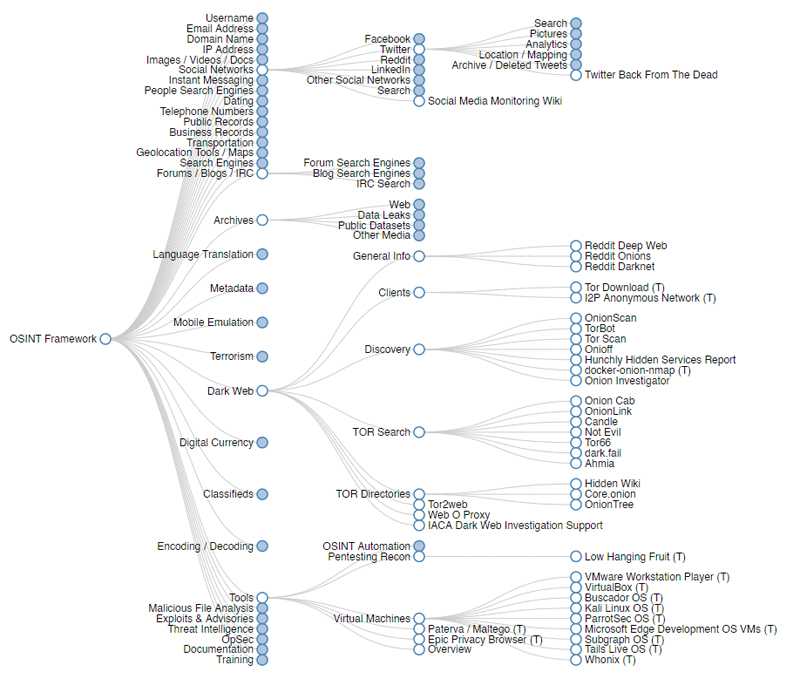
OSINT Framework
Interesting Reads!
- Insights
- February 27, 2021
Logging – Missing The Trees For The Forest
- Insights
- February 27, 2021
RAT’s in your Enterprise IT!
- Insights
- February 27, 2021
Security of Things
- Sales
- February 26, 2021





